About the Customer
The customer is a large Credit Card company with many external partners and customers who would benefit from using its internal products.
Key Challenge/Problem Statement
The Customer has partners that require a secure connection to the Customer’s internal applications. A partner needs to have a direct network connection to the Customer’s data center which can take up to 6 months for onboarding which can be a limiting factor for the Customer’s business.
Additionally, the Customer has to meet high compliance requirements for PII data in use while exposing these internal products to trusted partners. The Customer has to pass internal and external audits.
State of Customer’s Business Prior to Engagement
Prior to the engagement, Onboarding a partner was a painful process for the Customer. The process would typically take 5-6 months and at times was a limiting factor for the Customer’s business. Typically the Customer required the partner to:
- The client rents physical server space in an adjacent datacenter
- Submit multiple firewall access requests to the Customer
- Required to manage the physical hardware over the lifetime of that connection.
After the partner was onboarded, the Customer needed to enable these partners to create an arbitrary number of secure, PCI-compliant cloud-based applications that could connect to the Customer’s internal applications and potentially share PII data. These internal products are hosted inside the customer’s corporate data centers, but the data center model lacks the flexibility, scalability, and security controls the customer needs to safely and speedily onboard arbitrary numbers of external applications.
Proposed Solution & Architecture
The VR team worked with the Customer’s security, networking, and application teams to assess the current state and define the target operating model. The team then created targeted playbooks around runbooks around infrastructure and application security patterns for teams to adhere to.
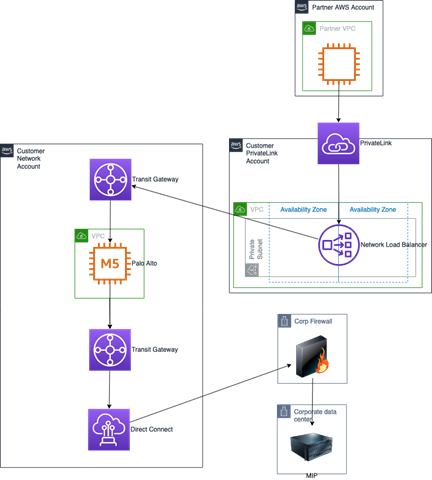
While new applications will be created in the cloud, the customer needed to maintain their internal applications in their data center during this stage of their journey. All traffic from these new applications to the on-premise environment was routed through an AWS Direct Connect link secured by the customer’s Palo Alto firewall applications that are hosted in AWS.
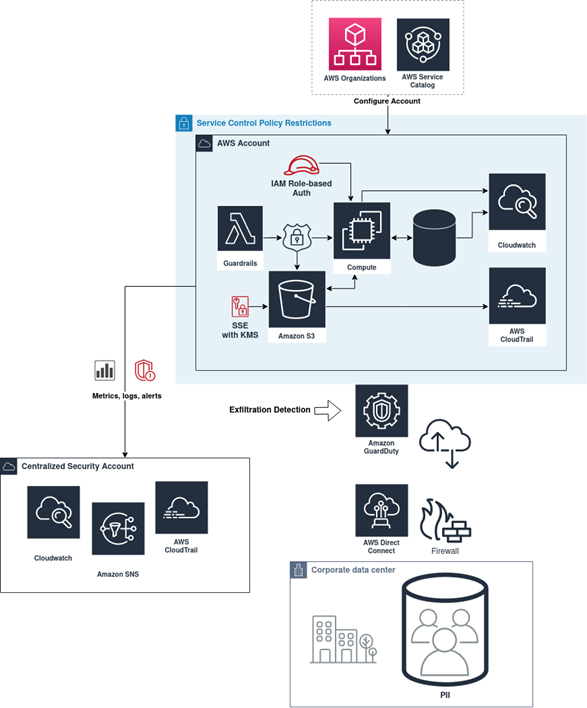
The solution had to allow the customer to create arbitrary numbers of standardized, restricted AWS accounts for external partners while still allowing partners the flexibility to build their applications. To support this functionality, a set of Service Catalog products were created to support vending AWS accounts with baseline functionality preconfigured. This baseline functionality includes SCP guardrails, OU assignment, and automated forwarding of CloudTrail, CloudWatch, and Network Load Balancing logs into Splunk Cloud.
To handle the security and PCI requirements, a cloud-based security model with a layered security approach was used to secure the infrastructure boundaries and add application-specific granular security controls.
- Guardrails and a secure-by-default model was put in place
- Granular resource and access policies were developed
- Detective and preventative controls were enabled to secure the environment
- Reactive controls were used to alert and remediate incidents
To limit actions for new applications within the various AWS accounts, Service Control Policies were used, which specify maximum permissions for new accounts, including actions available to the root user and any IAM Policies and Roles within those accounts, preventing cloud users and applications from violating established rules.
Astringent security review process was incorporated early in the SDLC, ensuring that every IAM Policy, Role, and Service Control Policy was restricted to the minimal necessary set of privileges before releasing into production environments, rather than restricting usage after noticing patterns
To provide a baseline for PCI-compliant data usage, the following guardrails, usually using AWS Lambda, are often invoked through CloudFormation Custom Resources inside of StackSets in each new account:
- Enforcement and remediation of encryption for persistent data stores using SSE-KMS, KMS Policies & IAM Role configuration
- Encryption of PII data in use is delegated to applications using client side encryption
- Detecting unauthorized data access, such as unauthorized detachment of EBS volumes and unauthorized modification of SCPs
- Data-classification identification and tagging: Tags, Managed Config Rules & Backup
- Principles of least privilege for IAM Roles: IAM Policies
- Rewriting default configurations, such as AWS accounts’ default open Security Groups
- Centralized application and cloud usage logging: CloudWatch and CloudTrail logging to central security-monitored account
AWS Services Used
- AWS Infrastructure Scripting – CloudFormation with Custom Resources
- AWS Compute Services – Lambda, EC2
- AWS Security, Identity, Compliance Services – IAM, KMS, Config, Secrets Manager, SCPs
- AWS Networking Services – VPC, Security Group, Direct Connect, Transit Gateways
- AWS Management and Governance Services – Organizations, CloudWatch, CloudTrail, GuardDuty, Security Hub, Landing Zone, Detective, Service Catalog
- AWS Application Integration Services – EventBridge, SNS, SQS
- AWS Frameworks – Landing Zone
Third-party applications or solutions used
- Palo Alto Networks Firewall and Panorama
- IBM Netcool and OMNIbus
- Splunk Cloud
Outcome Metrics
- 500% improvement in onboarding time for partners
- >10 clients expected to create applications in the cloud to interface with the customer
- 100% increase in security and compliance controls to help new applications pass an audit
Summary
By engaging with AWS and Vertical Relevance, the Customer was provided with a mechanism to create new AWS environments quickly and ultimately decreased their onboarding time for partners which materially improves their business. Additionally, the solution enabled the Customer to pass internal and external audits.