How a world-leading payments company deployed guardrails to ensure compliance requirements are met
About the Customer
The Customer is a large payments technology company that delivers innovative software and services to customers globally. This company provides a large variety of services such as the issuance of payment cards, loyalty card programs, and payment processing.
Key Challenge/Problem Statement
The customer is currently going through a transformation and moving several portfolios of applications from mainframes to AWS or AWS Outposts. This move requires each application to go through a complete security assessment to ensure compliance with the Payment Card Industries Digital Security Specification (PCI). The findings of this assessment revealed several flaws in their manual security and compliance processes. Consequently, the customer wanted to implement detective controls, automatic remediation for findings that are non-intrusive, and automated alerting and ticket creation for findings that are intrusive. The customer also wanted to enhance the security of their applications through code testing and pipeline scanning.
State of Customer’s Business Prior to Engagement
Prior to our engagement with the Customer, they already had several workloads within AWS. These workloads consisted of various SaaS products, reporting systems, and logging strategies that were largely manual and decentralized and inconsistent from account to account. The customer’s CI/CD process leveraged Terraform for infrastructure deployment and Jenkins to manage the pipeline. There were already some manual controls in place to secure the environment, but across many of the accounts, Security Hub was showing various non-compliant resources.
Another challenge with the customer’s existing implementation was working around the existing infrastructure and ensuring that remediation actions wouldn’t cause unforeseen downtime. Since the customer was concerned that changes may cause downtime and violate Service Level Agreements (SLA) with their customers, they were often neglecting to modify non-compliant resources.
Proposed Solution & Architecture
After identifying gaps in their approach to PCI security and compliance controls, we designed and implemented a centralized solution for compliance monitoring and automated remediation.
Auto-Remediation Framework
During our initial review of their internal processes for security events, we observed that it was very labor-intensive. Every incident that came into their system was flagged and evaluated using a runbook which would advise their Security Operations Center to manually complete the following steps:
- Gather the appropriate artifacts
- Remediate the issue
- Notify the appropriate teams
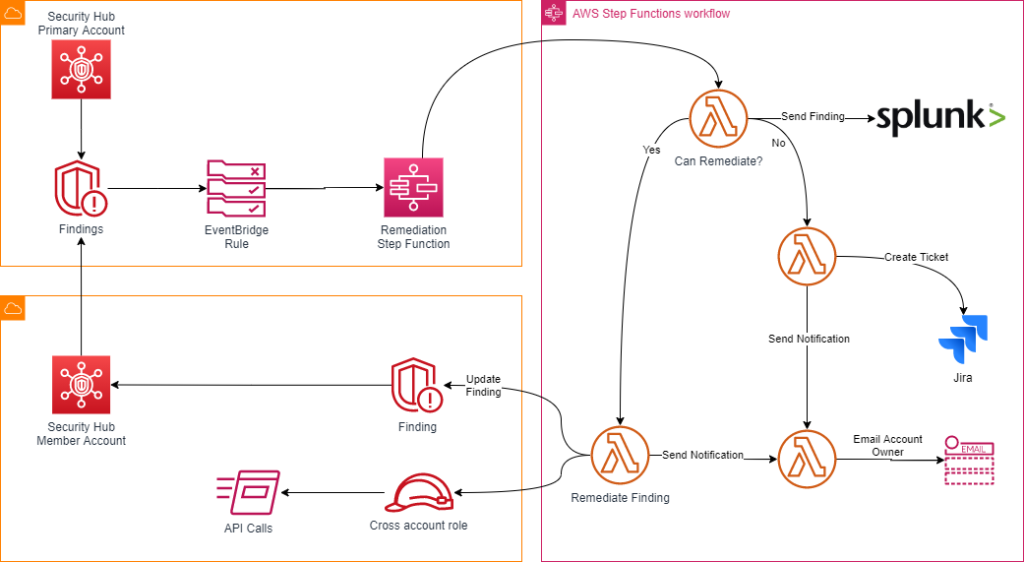
To address the shortcomings of this process, our solution automated the remediation of certain event types based on findings that would come into Security Hub. Findings were sent to Event Bridge which would then initiate a Step Function State Machine to process the finding. Via the step function, we would gather artifacts related to the finding, automatically remediate if the finding was a candidate for remediation, and then send out notifications based on the type of finding and level of alert. The notification system had custom integrations to Splunk, Jira, and Email as requested by the Customer.
The process we implemented was as follows:
Figure-01
Open Policy Agent
As part of the minimum-security baseline, we implemented Open Policy Agent checks within their CI/CD pipeline to automatically evaluate Infrastructure as Code (IaC) templates to prevent the deployment of non-compliant resource configurations (disabling key services, over-permissive security groups, unauthorized service changes, etc). In addition, we implemented reviews leveraging static analysis tools to evaluate their code.
By implementing this suite of custom application testing checks prior to every update to the application infrastructure and code, we were able to automate the preventative controls to ensure the security and compliance of the application was not impacted by changes.
Managed Config Rules
As part of a minimum-security baseline, we implemented 30+ custom AWS Config Rules to provide for continuous monitoring of resources within the Customer environment.
Security Control Policies
During our review of their current AWS state, we identified gaps around the Service Control Policies (SCP) that were in place. We designed several SCPs to put additional permission boundaries around service creation and modification.
Alerting Framework
Our solution enabled the customer to automatically receive alerts based on Log Filter Metrics and CloudWatch Alarms. We had the Log Filter Metrics and CloudWatch Alarm events pointed to an SNS topic with an SQS queue subscribed to the topic and a Lambda listener that was triggered by the SQS queue. This Lambda listener processed the event and created a custom finding to send to Security Hub. This automated process allowed the Security Team to have a single Dashboard where all findings would be captured from within the AWS Ecosystem.
AWS Services Used
AWS Compute Services – Lambda, Step Functions
AWS Storage Services – S3
AWS Management and Governance Services – CloudWatch, Config, CloudTrail, Organizations
AWS Security, Identity, Compliance Services – IAM, Key Management Service, GuardDuty, Security Hub
Third-party applications or solutions used
- Jenkins
- Terraform
- Splunk/Phantom
- Open Policy Agent
Outcome Metrics
- Increased security and compliance controls enabled the Customer to pass a PCI audit
- 15+ remediation event use cases were identified and implemented
- Application and IaC code went through reviews to catch any security issues
Summary
Vertical Relevance was able to bring our expertise to a large enterprise Customer by identifying security gaps and implementing controls to create a proper security baseline. Utilizing our unique skill set we were able to create automated processes to ensure that their systems were compliant with PCI standards and able to pass an audit. These solutions allowed the Customer to modernize their mainframe applications and move them into AWS.